
Key point: In this post: (1) increase in ECPA litigation as courts extend “crime tort” exception beyond health care; (2) service provider wins again against wiretapping claim; (3) defendants lose standing arguments in federal court; (4) VPPA circuit split widens as courts reject existing tests to determine whether disclosure of PII occurred; and (5) first PTFA decision in 15 years is issued, with more likely to come.
Welcome to our monthly update on how courts across the U.S. have handled privacy litigation involving website tools such as cookies, pixels, session replay, and similar technologies. In this post, we cover decisions from January 2026. And there were a lot of decisions. Courts issued twice as many California Invasion of Privacy Act (CIPA) wiretapping decisions in January 2026 than in December 2025.
Many courts are currently handling data privacy cases across the U.S. Although illustrative, this update is not intended to be exhaustive. If there is another area of data privacy litigation you would like to know more about, please reach out. The contents provided below are time-sensitive and subject to change. If you are not already subscribed to our blog, consider doing so to stay updated. If you are interested in tracking developments between blog posts, consider following us on LinkedIn.
1. Increase in Electronic Communications Privacy Act (ECPA) litigation as courts find “crime tort” exception met and deny motions to dismiss based on defendant’s consent.
California has remained the focus of privacy litigation over the past several years, with many claims brought under its wiretapping statute, Section 631 of the CIPA.
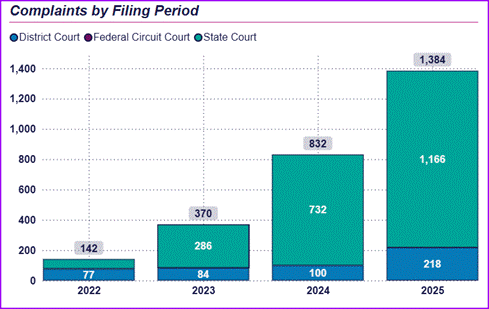
Source: Troutman Pepper Locke Litigation Tracker
This heavy reliance on CIPA has drawn legislative focus, with Senate Bill 690 intended to curtail use of the statute against websites’ use of cookies, pixels, and other tracking technology that is used for a “commercial business purpose.” Plaintiffs are increasingly filing wiretapping lawsuits that allege violation of the federal wiretapping act, which was introduced as part of the ECPA and is codified as 18 U.S.C. §§ 2510 et seq. Many of these claims allege both violation of CIPA and the ECPA, while others are being brought in courts outside California.
Although CIPA and the ECPA are often analyzed together, there are some critical differences. The ECPA provides statutory damages of $10,000 compared to CIPA’s $5,000, making it a more attractive cause of action for plaintiffs. It is also easier for defendants to dismiss a claim at the pleading stage, however, because the ECPA is a “one party consent” statute, which means only one party to the communication — such as the defendant website — must consent to the information being shared with third parties such as tracking technology and social media companies. When the interception occurs in furtherance of a crime or tort, however, the “one party” exception does not apply. Plaintiffs have so far largely focused on pixel use by health care websites within their patient portal, which courts have largely found sufficient to invoke the crime-tort exception. We are now seeing ECPA decisions that consider whether non-health care defendants have also committed a tort such that they must obtain plaintiffs’ consent to share the information with the third parties.
Seven decisions issued in January 2026 considered whether the plaintiffs had alleged the crime-tort exception applied. Five of these seven decisions found it did and denied the motion to dismiss.
One court from the Central District of California and one from the Northern District of California held the exception did not apply and granted the motions to dismiss. The Central District of California decision dismissed an ECPA claim against a defendant who provided mental health services through its website. The court criticized the plaintiff’s second amended complaint for not including any facts that “suggest [the defendant] intercepted and/or disclosed this information with violations of Health Insurance Portability and Accountability Act (HIPAA) as the ‘primary motivation or a determining factor.’” A decision from a Northern District of California court also granted a motion to dismiss by a defendant who operated a website that allowed users to manage their student loans. The plaintiffs alleged the defendant violated the Gramm-Leach-Bliley Act and the California Financial Information Privacy Act and thus the crime-tort exception applied. The court disagreed, finding the plaintiff failed to allege how the defendant violated these laws or that the violation was the purpose for the interception. As with the Central District of California’s decision discussed immediately above, this court also focused on the plaintiff’s allegations that the defendant used the tracking technology for financial gain.
The remaining five decisions found the crime-tort exception applied and denied the motions to dismiss. In one decision, issued by the Southern District of California, the plaintiff alleged he scheduled medical consultations and appointments on a website that used tracking technologies. The defendant argued that “[m]uch like the defendant in [a previous decision against a retail pharmaceutical company] . . . any interception of Plaintiff’s medical information that was passed on to Facebook through the use of Facebook Tracking Pixel was for commercial purposes and therefore neither criminal nor tortious.” Although this argument may have been accepted by the judges in two cases discussed above, this judge rejected the argument and denied the motion to dismiss. Another decision involving a retail footwear company also rejected the defendant’s argument that “where a defendant’s primary motivation is to make money, the exception is inapplicable.”
Three of these five decisions were against defendants who were registered data brokers. A January 6 decision from the Northern District of California rejected the defendant’s argument that the crime-tort exception was inapplicable because the defendant’s primary motivation was to make money, not injure the plaintiff tortiously. The court found the “disclosure and use of Plaintiff’s information for advertising can plausibly constitute an independent invasion of privacy beyond the act of intercepting the information alone, satisfying the crime-tort exception.” Twenty-one days later, another Northern District of California judge issued two nearly identical decisions denying motions to dismiss ECPA claims against two different data brokers. The judge found the plaintiff had stated claims for intrusion upon seclusion and invasion of privacy and therefore satisfied the crime-tort exception. The court rejected the defendant’s “primary motivation” arguments.
The final decision was against an online college where the plaintiffs alleged violation of both the Video Privacy Protection Act (VPPA) and the ECPA. This is the only ECPA decision we are covering this month that comes from a court outside California. The plaintiff alleged the defendant’s actions violated FERPA. A Northern District of Illinois court held the plaintiff adequately alleged the defendant procured third-party entities to intercept communications and obtain data from students “despite being protected from disclosure by law.”
The number of complaints filed that allege violation of the ECPA is already on the rise, as shown in the chart below. The denial of these motions to dismiss suggests we will continue to see an increase in these claims.
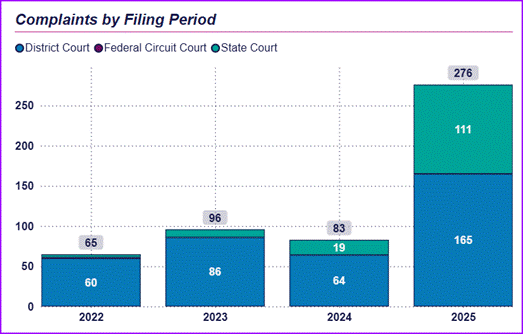
Source: Troutman Pepper Locke Litigation Tracker
2. A service provider wins again against wiretapping claim.
A January 21 decision from a Northern District of California court dismissed claims against a defendant who provides a SaaS platform upon which many retailer websites are built. The plaintiff alleged the defendant’s payment processing services violated California’s wiretapping laws because information users intended to send to the retailer-website during checkout was also being shared with the defendant. This defendant previously won dismissal of the claim after the court found it lacked personal jurisdiction over the defendant. The U.S. Court of Appeals for the Ninth Circuit had originally affirmed but then reversed after taking the matter up en banc.
The decision was remanded to the district court, which again took up the defendant’s motion to dismiss on issues other than personal jurisdiction. This time, the court dismissed the wiretapping claim after finding the defendant lacked the required intent to infringe. The court noted the defendant’s policies required the retailer websites that used the platform to obtain users’ consent and thus intended to only receive information where users had consented to the sharing. The court then dismissed the plaintiff’s claims for intrusion upon seclusion, invasion of privacy, and violation of the California Comprehensive Computer Data Access and Fraud Act (CDAFA) (Cal. Penal Code § 502) for the same reason.
This decision likely means plaintiffs will continue to target the websites that use such platforms rather than the platform providers. A January 22 decision from a Central District of California court rejected a similar “intent” argument made by a website owner after finding that the plaintiff plausibly pleaded the defendant knew or should have known the tracking technology would track visitor actions, send the third party information about the website visitors and the pages they visited, and provide better targeting for the defendant’s products and services to interested customers.
3. More courts reject defendants’ argument that plaintiffs lack standing in CIPA claims.
In August 2025, the Ninth Circuit issued its Popa decision, which affirmed a district court’s dismissal of a claim and finding that the plaintiff failed to allege a concrete injury related to a website’s use of session replay technology. Defendants have since then routinely argued plaintiffs lack standing to bring suit in federal court because violation of CIPA is insufficient to allege a concrete harm required to establish standing.
In January 2026, six courts considered these claims. Five courts denied these arguments and only one granted the motion to dismiss after finding the plaintiff lacked standing. The Northern District of California issued four of these five decisions, and only one judge issued more than one of the decisions. On January 6, a decision found the plaintiff’s allegations that the defendant, a data broker, had tracked the plaintiffs “across the internet” were sufficient to plead an injury conferring Article III standing and to state a claim for intrusion upon seclusion. On January 12, the same judge issued a decision denying the defendant’s standing argument where the plaintiff alleged the defendant tracked third-party application users’ geolocation through a software development kit (SDK). The court distinguished Popa by finding the accused activity in this case was “materially more invasive than the more limited tracking at issue” in Popa.
On January 27, a different Northern District of California judge denied a motion to dismiss for lack of standing where the plaintiff alleged the defendant “outright lied” about its use of tracking technology on the website by informing users that the website would not track users who opted out. The court rejected the defendant’s standing argument and distinguished Popa to find the plaintiff’s harm was similar to the common law claim public disclosure of private facts.
Two days later, yet another judge issued a decision that held the plaintiff had established standing by asserting that website users are harmed not just by the collection of data, but by being identified and “linked to comprehensive, non-anonymous profiles” that “are offered up for sale to a near endless supply of advertisers without knowledge or consent.” The court distinguished Popa because the tracking in that case was limited to the defendant’s website and not tracking across websites.
A Central District of California court also issued a decision denying the defendant’s motion to dismiss under Rule 12(b)(1). In that case, the defendant argued the plaintiff failed to allege the defendant captured any sensitive, intimate, or private facts as to plaintiff or visitors generally. The court disagreed and found the plaintiff alleged the defendant’s tracking practices enabled it to regularly collect personalized information when the defendant visited the website.
Although one court dismissed the plaintiff’s ECPA claim after finding the plaintiff lacked standing to bring the claim in federal court, the decision distinguished tracking technology cases such as the ones discussed above. The plaintiff’s claim was instead based on the defendant’s use of AI to record telephone conversations as part of providing administrative services to dental clinics.
Collectively, these decisions show defendants cannot merely rely on the Ninth Circuit’s Popa decision to defeat claims brought in federal court. Where the plaintiff can defeat dismissal of a tort claim such as invasion of privacy, defendants are less likely to win dismissal by showing the plaintiff has failed to establish standing under Article III.
4. Courts in jurisdictions that have not adopted either the “ordinary observer” or “reasonably foreseeable” tests find disclosure of Facebook ID meets “personally identifiable information (PII)” requirement under VPPA.
Courts are currently split as to what test to apply to determine whether a defendant has disclosed a consumer’s PII:
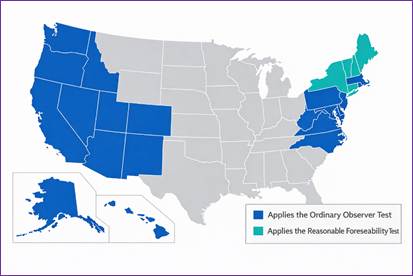
The U.S. Court of Appeals for the First Circuit — including Maine, Massachusetts, New Hampshire, and Rhode Island — applies the “reasonable foreseeability” standard, under which PII is not limited to information that explicitly names a person, but also includes information disclosed to a third party that is “reasonably and foreseeably likely to reveal which videos the plaintiff has obtained.” The U.S. Courts of Appeals for the Second, Third, and Ninth Circuits — which include Alaska, Arizona, California, Connecticut, Delaware, Hawaii, Idaho, Montana, New Jersey, New York, Nevada, Oregon, Pennsylvania, Vermont, and Washington — apply the “ordinary observer test,” under which a violation occurs only if an ordinary person, without specialized knowledge or tools, could use the disclosed information to identify a consumer’s video viewing history. Some courts that apply the ordinary observer standard (mostly those in the Second Circuit) have held the standard forecloses claims that use of the Meta pixel discloses a consumer’s PII, while other courts have allowed claims based on the Meta pixel to continue past the pleading stage. We have covered this “split within a split” in a previous article.
In January 2026, two courts held disclosure of the Facebook pixel meets the PII requirement under the VPPA. Critically, these courts are in circuits that have not adopted either the ordinary observer or the reasonable foreseeability tests and may indicate the rise of a third faction of courts within this split.
On January 13, a Northern District of Illinois court issued a decision finding an educational institution defendant violated the VPPA when it shared information about what online courses students viewed with Meta. In determining whether the defendant had disclosed plaintiff’s PII, the court acknowledged the circuit split on this issue. Although the court found it unnecessary to choose either approach “because the result is the same under both tests,” the court rejected the Second Circuit’s interpretation of the ordinary person test, which has “effectively shut the door for Pixel-based VPPA claims.” The court found it “nonsensical” to “categorize information as PII based on its format, rather than the type of information conveyed” as “such a system would create a significant loophole in the VPPA that would allow to evade liability by formatting PII into code.” Ultimately, the court found the information alleged in the complaint is “plainly sufficient for an ordinary person, or Meta, to determine a person’s Facebook ID.” Although the court denied the motion to dismiss the VPPA claim, the court found there were insufficient allegations as to the non-Facebook tracking technologies.
On January 23, an Eastern District of Missouri court also rejected both the “ordinary observer” and the “reasonably foreseeable” tests as “unnecessary” and “extra-textual.” The court found the disclosure of the Facebook ID sufficient because “[t]he statute does not let companies distribute information so long as they encrypt it first. It is the transfer of protected information to the receiver that the Act prohibits, regardless of the manner of transmission.”
The U.S. Supreme Court recently made headlines by granting certiorari to resolve when a plaintiff qualifies as a “consumer” under the VPPA. Although SCOTUS recently declined to hear an appeal of one of the courts that had adopted the “ordinary consumer” standard, this continued split may suggest we see another VPPA case in the Court’s next term.
5. The first decision since 2010 to address the Colorado Prevention of Telemarketing Fraud Act.
In July 2025, we covered what was then an emerging trend as plaintiffs filed a series of putative class action lawsuits targeting data companies that possessed consumers’ cellular telephone numbers. The lawsuits alleged violation of Colorado’s Prevention of Telemarketing Fraud Act (PTFA), which prohibits knowingly listing a cellular telephone in a directory for a commercial purpose.
As of July 2025, only three decisions had cited the PTFA, with the most recent published decision issued in May 2010. Fifteen years, seven months, and 25 days after that decision, another court has now addressed the PTFA. On January 13, a Central District of California court issued a decision addressing a PTFA claim made against a defendant who provides lead services for B2B companies. The decision denied the defendant’s motion to transfer the matter to Colorado and denied the defendant’s motion to dismiss the complaint. There are several motions to dismiss pending in courts across the U.S. and we will likely continue to see additional guidance on this statute in the months to come.